What is Zero Trust security?
- DigiSOC

- Aug 29, 2025
- 3 min read
The model that eliminates implicit trust in cybersecurity. Zero Trust security is a modern approach to digital protection based on a simple but powerful idea: never trust anyone or anything by default, whether inside or outside your network. Every user, device, or application must prove who they are and what permissions they have every time they attempt to access a resource, regardless of whether they are already "inside" the organization.
Why is Zero Trust so important?
The traditional security model, based on protecting the network perimeter, is no longer sufficient. Today, organizations operate in much larger, more complex, and distributed environments than just a decade ago.
For years, companies focused on creating digital "walls of protection" with firewalls and controls that protected external access. Any user or device that gained access was considered trusted, giving them free rein to move within the network and access resources, applications, and data.
But the world has changed. Digital transformation, remote work, the use of cloud services, mobile devices, IoT, and software as a service (SaaS) have blurred the boundaries of that perimeter. Corporate networks are no longer confined to an office: they extend across the globe.
This growth also brought an increase in the attack surface, making companies more vulnerable to:
Data breaches.
Ransomware.
Insider threats.
Lateral movements of attackers.
In this new landscape, perimeter-centric defenses simply aren't enough. It was in this context that, in 2010, John Kindervag (analyst at Forrester Research) proposed the concept of Zero Trust, an approach that breaks with the idea of implicit trust and places control on every resource, not just the input.
The key?
Every request, user, or device is considered potentially risky until proven otherwise. Regardless of whether you're already on the network, you must re-authenticate and re-authorize each time you want to access something new.
This continuous validation model allows:
Limit unnecessary access.
Detect anomalous behavior.
Reduce the impact of an attack if one occurs.
Zero Trust doesn't just improve security, it redefines it.
Fundamental principles of Zero Trust security
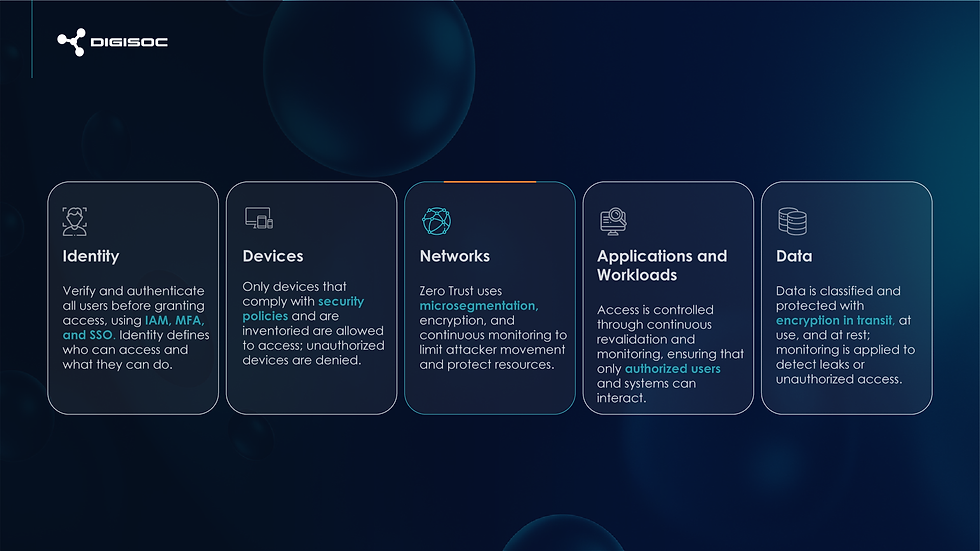
Continuous authentication and strict verification: Every user, device, or entity must be rigorously and consistently authenticated and authorized before accessing any resource, regardless of whether it's inside or outside the corporate network. This includes the use of multi-factor authentication (MFA) and contextual assessment (identity, location, device status, etc.) to validate each access request.
Least privilege access: Users and devices are granted only the minimum level of access necessary to perform their tasks. This limits the scope of potential attacks and reduces the exposure surface by implementing controls such as just-in-time access, specific roles, and periodic permission reviews.
Assume breaches or leaks (assume attacks): The assumption is that breaches can occur at any time. Therefore, the network is segmented into small zones (microsegmentation) to limit lateral movement by attackers, activity is continuously monitored, and visibility is maximized to quickly detect and respond to threats.
These principles work together to eliminate implicit trust and protect resources through constant verification, restricted access, and a proactive stance against potential attacks.
Pillars of the Zero Trust security model
What is Zero Trust Network Access (ZTNA)?
Zero Trust Network Access (ZTNA) is a technology and security model that provides secure remote access to an organization's internal applications and services, based on the fundamental principle of not trusting anyone or anything without strict and continuous verification. Unlike virtual private networks (VPNs), which grant full network access, ZTNA grants access only to specific applications or resources for which the user is authorized, following granular access control policies.
How does ZTNA work?
Isolating application access from network access | ZTNA separates application access from general network access, reducing risks such as the spread of malware from compromised devices. |
Output-only connections | The user initiates a secure connection to the application, but the network and applications remain invisible to unauthorized users, creating a “dark web” where IP addresses are not exposed to the Internet. |
Native app segmentation | Access is granted individually to each authorized application, preventing excessive access and lateral movement of attackers within the network. |
User-application approach | Authentication and authorization are prioritized based on user and device identity, rather than location or network, using end-to-end TLS encrypted tunnels. |
Main advantages

Information source:




Comments